Save Sensitive Data With Endpoint Protection

Endpoint encryption is the most important part of a company to protect and secure its data. We always take care of the fact that we shouldn’t give our ATM card’s PIN number to anyone or that we should lock our house securely before leaving it so why don’t we act that carefully when it comes to the protection of IT network of the company. These days, many companies hold sensitive or personal information about their consumers or they even need to guard confidential data related to the company itself.
People are getting more and more used to their phones, tablets and laptops. They start working on them when they are not even in office leaving behind the client details insecurely in their PC. The recent data breaches of celebs, that became the talk of the town, made us more aware about the repercussions and the need for endpoint management. But, then too we choose to ignore the fact that it can cost us almost everything if some important document gets breached.
If you are a company that works for client-satisfaction, then to maintain and protect the safety of their files should be a huge matter of concern for you. It is only then, that the client will feel satisfied and secure. This can only be done by endpoint protection.
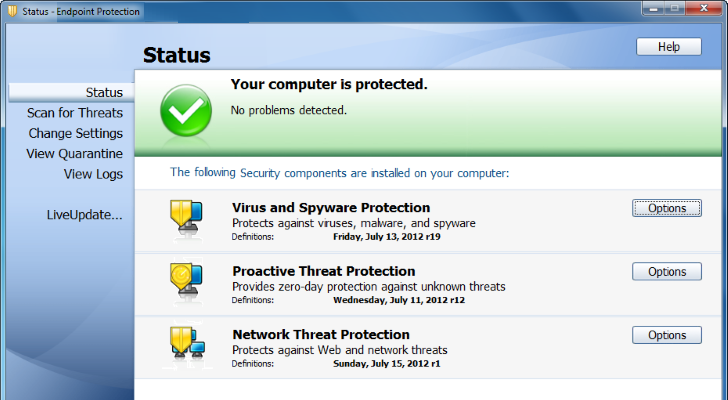
The endpoint security is a method to protect a corporate network. Whenever a file is accessed through a remote device like a mobile phone, laptop or a tablet, it starts looking for a threat. Each and every remote device that is connected to the network becomes a potential security threat. The endpoint protection is designed to shelter each endpoint created by the remote devices. Basically, endpoint security is an endpoint management system that comprises of security software which is situated on a centrally managed server within the network. This server updates the server whenever needed and also approves endpoint logins. That’s the reason why endpoint protection is becoming more and more common within the IT sector.
Different hardware and software packages are accessible for endpoint encryption. An encryption algorithm needs to be used to convert information. In some cases hard-disks are encrypted and in others the whole disk needs to be encrypted. The most common algorithm is Rijndael. There are others as well such as two fish, Serpent and MARS.
Security and speed of encryption affects the choice of algorithm. Once the disc is encrypted, it usually has a two-level authentication procedure. In the first level, the endpoint means is booted and in the second level the user has to login with a username and password. When the requested files are used, a copy of it is saved in the encrypted drive as well. This brings the file under scanner and the security system makes sure that it is not being used by a hacker ort a fraud.
Endpoint protection allows an administrator to maintain a user list to keep a track of the files and also for the recovery of some information in need of that sorts arise.
