
Top Five Cyber Security Myths
Cyber Security Basics The notorious scandals as well as unfortunate personal experience induced people in a constant state of doubt when it comes of...

Cyber Security Basics The notorious scandals as well as unfortunate personal experience induced people in a constant state of doubt when it comes of...

The motivation behind hackers has evolved noticeably over the last couple of years. Developing harmful viruses is less about “bragging rights” or satisfying the...

“Would you let someone walk into your home, take whatever they wanted and leave as if nothing had happened?“ No! Of course you wouldn’t....

You receive an email from your bank warning you that your account information needs to be updated urgently or else it will be suspended....

Are you making yourself a target for fraud? More and more often I am hearing stories of people who have had their accounts hacked....
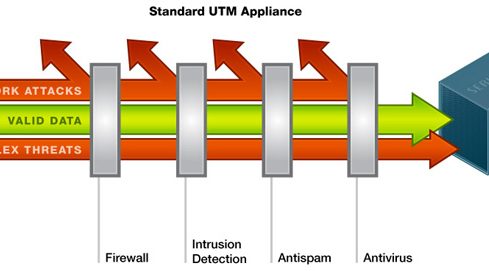
Addressing the issue of whether network security “really is as difficult as it seems,” Tracey said for some it is. But with what he...

Your PC has many “ports” which are vulnerable to attack from a hacker. These ports are used to communicate internally with your monitor or...

The Internet is a powerful tool for home-based businesses. If used effectively, it can be your best friend; but if you don’t secure your...

If you’ve given any thought to home security you’ve probably considered a closed circuit television monitoring system (better known as CCTV.) What you’ll have...

Today, more and more people are using their computers for everything from communication to online banking and investing to shopping. As we do these...