Cross-Site Scripting Attack Composition
A Cross-Site Scripting (XSS) attack describes a hacking method where one websites uses client-side script in order to bypass security methods and access controls. It takes advantage of vulnerability inherent in what is known as same origin policy.
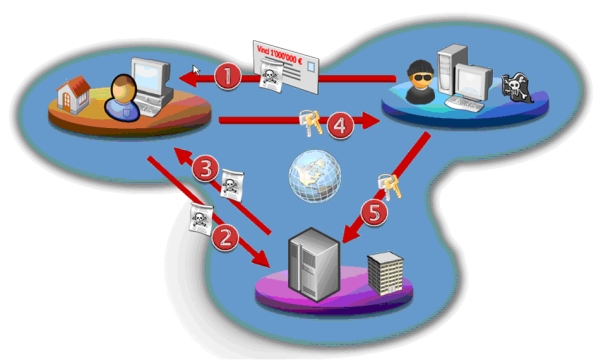
Same origin policy is a website standard that if content from a specific site has permission to access the resources on another site, then all content from that site will enable access to be granted.
Because the information looks like it comes from a trusted source, servers and plug-ins alike are vulnerable.
There are three basic types of attacks that fall under the XSS category. They include:
This is a server-side code preparation. A HTML response is offered to the user as a part of the content processing stage.
Data is preserved by the attacker on the web pages and they can gain access to protected information. For example, if a new user enters data during the initial set-up stage, that information can be sent to the hacker.
This is the most common type of XSS that allows the hacker to retrieve information via an unaware user.
With many of these forms of XSS attacks, users are the weakest link. They are sent a link in an email, or download code from a malicious website. This code then allows the hacker access to data and processes on the websites the user accesses. The user and the website owner are often unaware of the situation, and this attack can continue for a while before it is detected.
Often users clean their systems regularly and follow safe surfing policies while on the Web. These actions can reduce the number of attacks, or prevent them from wreaking too much havoc before they are removed. Not all users are this cautious, however, and hackers are becoming more sophisticated in their methods.
This means that companies can’t rely on users to prevent cross-site scripting attacks and they need to institute prevention measures in order to eliminate this threat. These measures can include the way websites are coded, the security software used to monitor the sites, and the options offered to users in order to help eliminate the potential methods hackers use to gain access to the back end processes to obtain information and change the programming.
XSS attacks account for two-thirds of the security breaches that occur on company websites. They also account for the type of viral codes discovered and removed from the client’s systems as well. This makes cross-site scripting attacks one of the top security threats a company needs to defend against in order to protect its websites. Companies need to make sure that security measures are not only put in place, but reviewed periodically and updated when necessary. Because technology changes quickly, even a sophisticated security software program can become out of date rapidly. It is important to keep apprised of changes in the way XSS attacks are used to breach web security measures, as well as new information on how to defeat them.
About author:
Olivia is the Director of Product Marketing at Veracode, an award-winning application security company specializing in secure software supply chain and other security breaches with effective risk assessment tools like XSS, http://www.veracode.com/security/xss, and web application security testing.
