
Network Security – The Real Vulnerabilities
Scenario: You work in a corporate environment in which you are, at least partially, responsible for network security. You have implemented a firewall, virus...

Scenario: You work in a corporate environment in which you are, at least partially, responsible for network security. You have implemented a firewall, virus...

Wireless Internet connections aren’t just convenient for you-they also may be convenient for hackers. Fortunately, it isn’t difficult to protect yourself. Wireless systems can...

Are you making yourself a target for fraud? More and more often I am hearing stories of people who have had their accounts hacked....

Setting up a wireless router is easy. Essentially you turn your cable or DSL modem off and your wireless router on. Then, you connect...

Recovery Toolbox for Zip was developed to fix corrupted archives in Zip format. File compression is very popular, it is used, when forwarding large...

Most people on the internet are good, honest people. However, there are some people browsing the internet who derive fun from poking around websites...
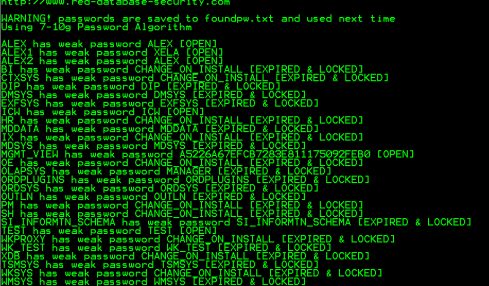
Passwords to access computer systems are usually stored, in some form, in a database in order for the system to perform password verification. To...

Check List for Linux Security Linux is an amazing operating system considering how it was originally created. It was a modest program written for...