
How Hackers Take Control of Your Computer
Your PC has many “ports” which are vulnerable to attack from a hacker. These ports are used to communicate internally with your monitor or...

Your PC has many “ports” which are vulnerable to attack from a hacker. These ports are used to communicate internally with your monitor or...

The Internet is a powerful tool for home-based businesses. If used effectively, it can be your best friend; but if you don’t secure your...
Running a business from home has its advantages, including no commute, a more accommodating work schedule, fresh coffee and home-cooked meals at any time...

Proxy sites enable the individual to access websites and servers through another server to keep the location and identity of the individual unknown. This...
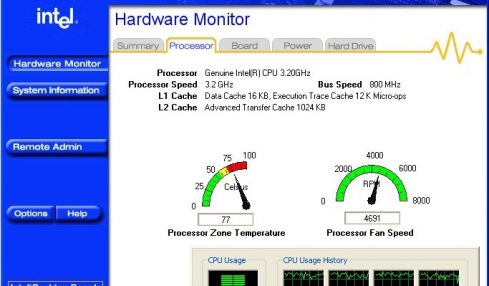
A computer temperature, as the name clearly states, is the temperature of your computer. This is largely a sum of various devices giving off...
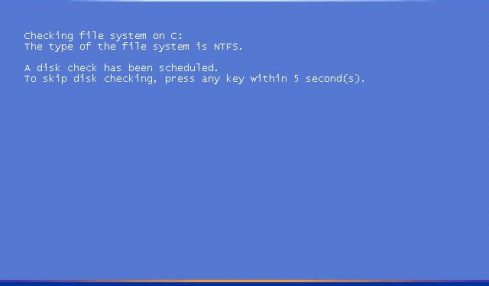
ScanDisk checks and repairs file systems and bad data clusters. ScanDisk is a system utility which is bundled with and all Microsoft Windows Operating...

11 Names you must know When a problem is properly identified, half of the battle is already won. You may not necessarily win the...

How To Choose: There are only a few main parts of the computer that truly make the difference between the others. As long as...

De-fragmenting your hard drive is an often neglected part of computer maintenance. If you ask most people how to de-fragment a hard drive they...

First lets talk about what a dedicated server is. A dedicated server is kind of what it sounds like. It is a server that...