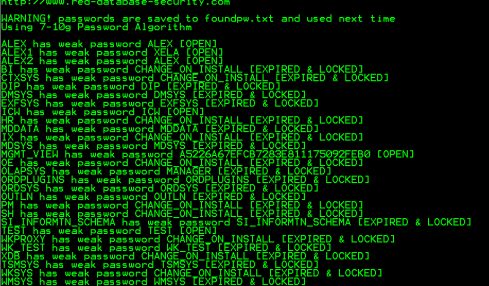
Background of Password cracking
Passwords to access computer systems are usually stored, in some form, in a database in order for the system to perform password verification. To...

Passwords to access computer systems are usually stored, in some form, in a database in order for the system to perform password verification. To...

A great number of our customers use file compression on a daily basis. RAR archiver is very popular and it is often used, when...
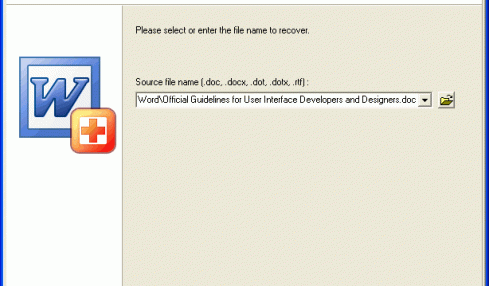
Recovery Toolbox for Word is a program for Word file repair, it helps to repair docx files, if it was not possible to prevent...
Ask Darin Myman about an email that should never have been sent, and he likely will tell you about a friend who was caught...

Wow, Charms are popular items these days. There are thousands of online businesses that sell Italian charms to all sorts of people who are...

There are several levels of security to SQL Server. At the a base level, in order to be granted get access to a SQL...

There are so many great things about the internet you know that there is going to be problems. And there are! Identity theft, fraud,...
No matter whether you are a student, homemaker, scientist, businessman, or other, it is more than likely that you need access to your computer...

So have you bought a new computer at home for yourself and for your kids? Your computer is sure going to be useful to...

Anti-spyware is software that protects computer users from spyware and other unwanted software. Anti-spyware programs secure the computers against the effort of malicious spyware,...